Published OnAugust 20, 2025August 20, 2025
The Command-and-Control Challenges Facing Global Defense at the Tactical Edge
DoD needs C2 networks that support data synching and data sharing – even without cloud/server connectivity

“The ability of near-peer adversaries to disrupt the current C2 networks of the US and its allies is growing at an alarming pace. This is a critical vulnerability that can undermine every part of our warfighting strategy; if we want to prevail in a future conflict, we need to start by making our data sharing capabilities more resilient and interoperable at the tactical edge – where battles are won or lost.” – Rear Admiral (Ret) Matthew J. Burns
In this article, we want to focus on data sharing, connectivity, and interoperability at the tactical edge, where warfighters are forward deployed and operations are decentralized. Within this arena, there are two urgent and interrelated challenges facing US and Allied military planners:
- The need for resilient, interoperable, “cloud-optional” connectivity
- The need to “backhaul” data from the operational edge to the enterprise
Let’s start by considering what a future conflict with a near-peer adversary might look like from a tactical command and control perspective.
To begin with, there would be multiple US Military and Allied command posts dispersed over a battlespace as large as the Pacific Ocean, some of them thousands of kilometers from regional headquarters locations.
Unlike Iraq or Afghanistan, in a conflict with a near-peer adversary, the US cannot assume communications and control dominance. Its technologies and networks must reflect this reality.
Each of these command posts will be responsible for hundreds or thousands of warfighters, as well as sophisticated military assets – vehicles, drones, long range fires, sensors, electronic warfare systems, etc. They will rely on thousands of tactical edge devices – UAS mission computers, ATAK handheld devices, surveillance systems, and MANET radio networks to feed their decision cycles. And of course, they will need to share data with headquarters units and coordinate with space, naval, aerial, or other domains.
But unlike in Iraq or Afghanistan, in a conflict with a near-peer adversary, the US military cannot assume seamless cloud/server connectivity, much less total communications and control dominance. Instead, these command posts will be facing an adversary with highly advanced electronic warfare capabilities.
These capabilities will disrupt the terrestrial and satellite communications links and hardware that are the backbone of the military’s communications and control architecture. US military planners today must assume that in a future military conflict, command posts may become “disconnected” from headquarters or other units – and still need to function effectively. Our command-and-control technologies and networks must reflect this reality.
Brittle vs. Resilient, “Cloud-Optional” Network Architectures
Throughout global defense and public safety, existing network architectures in which a centralized command post or operations center is responsible for data aggregation and dissemination, the loss of critical network links – especially links to cloud-based servers – is a constant vulnerability.
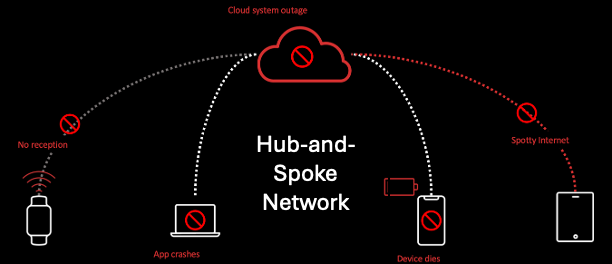
But these architectures are a reflection of technical limitations that no longer hold true; What if DoD had a data network with no single point of failure? What if it had a network where data synching and data sharing are possible, even without cloud/server connectivity?
This is achievable in a distributed database, in which each node is connected via multiple links to other nodes and the system automatically resolves differences in data amongst all. A distributed database architecture reduces brittleness and makes use of every available path to create causal consistency amongst all nodes, helping to not only move data, but also make sense of it.
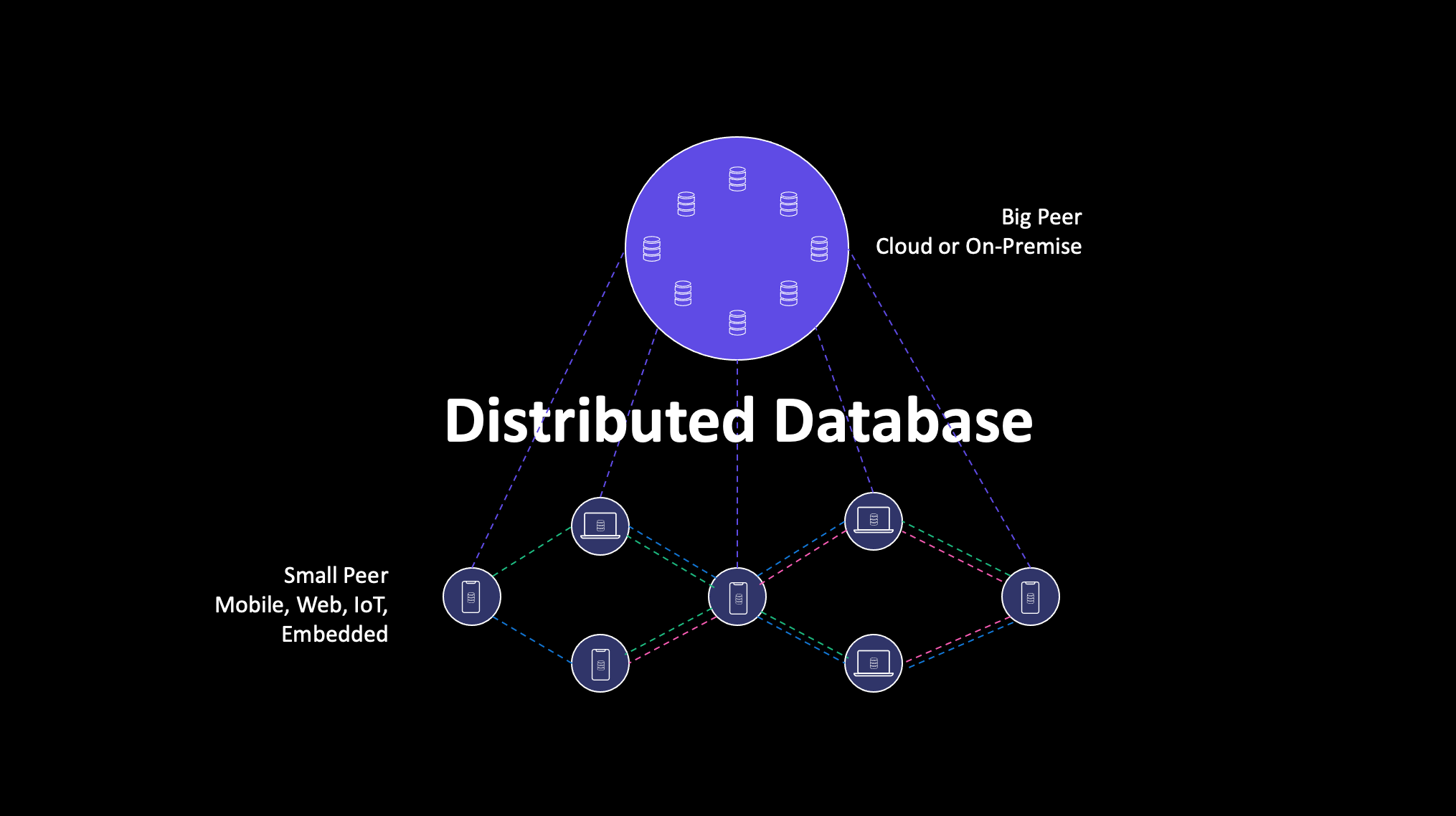
Getting Data From the Tactical Edge to the Enterprise: The “Backhaul” Challenge
In a future military conflict, the ability of DoD and its allies to act on data collected at the operational edge will be decisive. But in such a conflict, there will be huge amounts of data being collected while C2 assets are under attack. Given the limitations of current DoD connectivity and data sharing infrastructures, there is a risk of data flooding (too much unnecessary data being sent back all at once) and data latency (delays in data sharing) – both of which will jeopardize decision-making.
This is the data “backhaul” problem, i.e. how do tactical military units or command posts get critical data from the edge back to “the enterprise”, i.e., a regional command HQ or even the Pentagon, where the data and intel can be analyzed and used.
The DoD and its Allies need technologies that share only data that is needed AND that can reduce bottlenecks in data transmission through a data mesh networking approach. Ditto’s distributed database not only creates consistency across nodes, it also supports specific data-type queries, ensuring that only mission critical data moves over the already congested networks. For instance, a logistics cell may be more focused on monitoring supply levels at the tactical edge than intel reports, and could set data queries to pull only that information.
Conclusion: Enabling Operational Resilience
DoD’s need for robust data sharing and connectivity has never been greater. And yet the US military can no longer assume command and control technology dominance, especially at the tactical edge. Not only do adversaries have sophisticated electronic warfare capabilities, but they are also constantly innovating and seeking to overcome US military advantages via their own countermeasures.
This new reality calls for new types of data sharing and connectivity, technologies that can make our current C2 systems more resilient, and more capable of responding and adapting to emerging threats. These technologies exist today, and by deploying them, we can ensure that warfighters and military assets can be operationally effective even when traditional C2 infrastructures are disrupted.
David DeVries is the Public Sector GTM Director at Ditto, with over a decade of experience driving growth across federal and commercial sectors. Visit https://www.ditto.com/solutions/public-sector to learn more about the work Dave and team are doing to ensure operational resilience and edge device connectivity.




